Intel AMT Vulnerability Shows Intel’s Management Engine Can Be Dangerous

Intel published a security advisory for a privilege escalation bug in its Active Management Technology (AMT). The vulnerability exposes all Intel chip…
Intel published a security advisory about a vulnerability that affects Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel Small Business Technology (SBT) software. The company also released detection and mitigation guides, but the firmware updates would have to come from OEMs. The vulnerability shows that Intel ME’s out-of-bound functionality, such as installing software remotely on PCs, could pose serious dangers to systems, as some free software activists have already warned.
Intel ME And AMT
Intel’s Management Engine (ME) is a separate computing environment working on Intel’s chips that comes with its own separate processor, whereas AMT is the software that provides the ME functionality to system administrators. According to some researchers, the ME has access to “everything,” including network, memory, and the cryptography engine. AMT and ME can also be accessed remotely, which Intel has argued that is a feature of its processors:
Intel Active Management Technology (Intel AMT) allows IT or managed service providers to better discover, repair, and protect their networked computing assets. Intel AMT enables IT or managed service providers to manage and repair not only their PC assets, but workstations and entry servers as well, utilizing the same infrastructure and tools across platforms for management consistency. For embedded developers, this means that devices can be diagnosed and repaired remotely, ultimately lowering IT support costs.
All of this has led free software activists, such as those working on Libreboot (a free software alternative to UEFI), to brand it a “backdoor.” Even without considering it a backdoor, the Libreboot founder has argued that the capabilities of Intel ME can be exploited by others once vulnerabilities in it are found:
Intel Management Engine with its proprietary firmware has complete access to and control over the PC: it can power on or shutdown the PC, read all open files, examine all running applications, track all keys pressed and mouse movements, and even capture or display images on the screen.
And it has a network interface that is demonstrably insecure, which can allow an attacker on the network to inject rootkits that completely compromise the PC and can report to the attacker all activities performed on the PC. It is a threat to freedom, security, and privacy that can’t be ignored.
AMT Vulnerability And Mitigations
A vulnerability was found earlier this year by Maksim Malyutin from Embedi that affects Intel’s AMT, the software that runs in the ME environment, as well as ISM and Intel SBT versions 6.x through 11.6.
The vulnerability allows privilege escalation on a user’s machine, and it could be exploited by attackers to take over and possibly even decrypt encrypted hardware (unless the PC comes with a TPM chip). The vulnerability affects all Intel chips from 2008 up to the latest Intel Kaby Lake generation.
Intel said that this particular vulnerability doesn’t affect consumer chips. However, free software activists’ arguments about Intel ME’s dangers in general likely hold true, as this vulnerability may not be the only one out there that exists or that Intel is willing to make public. SemiAccurate said yesterday that it told Intel about this vulnerability more than five years ago, but it was mostly ignored by Intel executives. Intel didn’t confirm whether or not this is true.
Enterprise customers are affected as described below:
An unprivileged network attacker could gain system privileges to provisioned Intel manageability SKUs: Intel Active Management Technology (AMT) and Intel Standard Manageability (ISM).
An unprivileged local attacker could provision manageability features gaining unprivileged network or local system privileges on Intel manageability SKUs: Intel Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel® Small Business Technology (SBT)
Intel released a detection guide so you can see if your company’s machines are affected by the vulnerability. You can also check in the table below to see which versions of the SBT firmware versions are impacted and which resolve the issue.
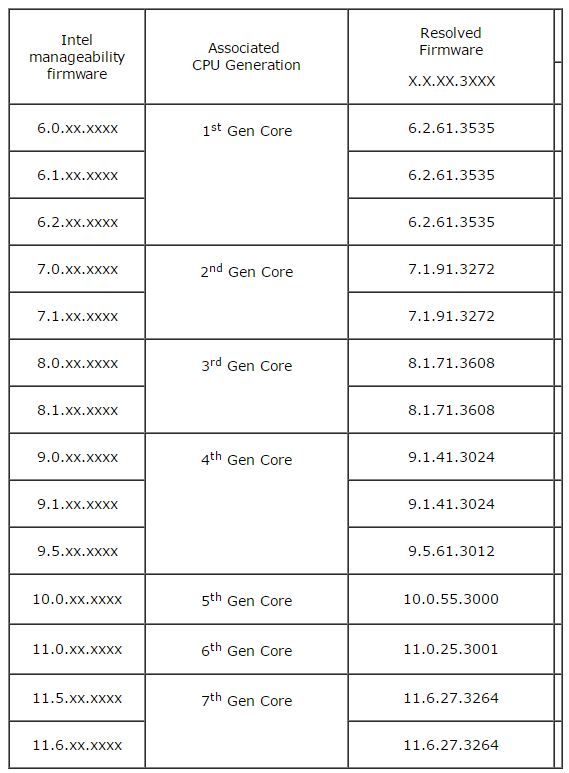
The main problem may be that the firmware needs to be released by the makers of those computers, and some of them may not release firmware updates for machines that are more than a few years old. In that case, you may want to follow Intel’s mitigation guide for how to protect your computers against exploits that use this vulnerability.
Intel ME’s Future In Question
The free software and Linux communities, as well as some companies such as Purism, have been working on ways to disable the Intel ME and AMT software, with some degree of success. Mainly, it’s difficult to fully disable Intel ME because, it seems, Intel designed it that way; usually, if you try to hack and disable the ME, the computer will shut down.
If Intel redesigned the ME environment on its chips, it should be possible to allow users to easily and completely disable Intel ME. If the company decides against that, it may be less of a technical decision and more of a political and strategic one. Intel may not want to give up on certain CPU features that the company may consider mandatory, such as DRM.
The free software community has also lately been encouraging AMD to open source the firmware for its ARM-based Platform Security Processor (PSP), which is the equivalent to Intel’s ME. It’s not clear whether or not open sourcing the firmware would actually fix any of the dangers these types of environments pose, but it may be a step in the right direction. It could also be a strategic advantage for AMD, if Intel continues to ignore these concerns.
Tom’s Hardware asked Intel if it plans to alleviate these concerns in any way in the future (such as by creating ME-less chips, as Purism has proposed), but we haven’t yet received a response.